Container Previews
Deploy container image previews with enterprise-grade security and performance. Namespace's Previews enable development teams to test applications in isolated, ephemeral environments accessible to the whole team enabling quick feedback cycles.
Why Namespace Previews?
Getting Started
Ensure access to Namespace
Using the CLI, log into your workspace. If you're accessing Namespace from a cloud provider or your CI platform, we recommend to set up workflow federation instead.
$ nsc loginStart your preview
$ nsc run --image nginx -p 80
# Prints a preview URL, e.g.: https://4bi2reg-grijlvs6ciapa.ord2.namespaced.appDone!
Your preview is now available. All requests to the exposed URL require authentication.
How it works
Namespace preview clusters build on Namespace Compute to deliver interactive access to a flexible, isolated test environment. Any public images, or any image present in your private container registry can seamlessly run in a preview. Namespace generates public, authenticated ingress URLs using managed TLS certificates, whether you use a Namespace-provided app domain, or employ custom domain configurations.
Namespace ingresses preserve original headers for application-level routing and support path-based and header-based routing within your application.
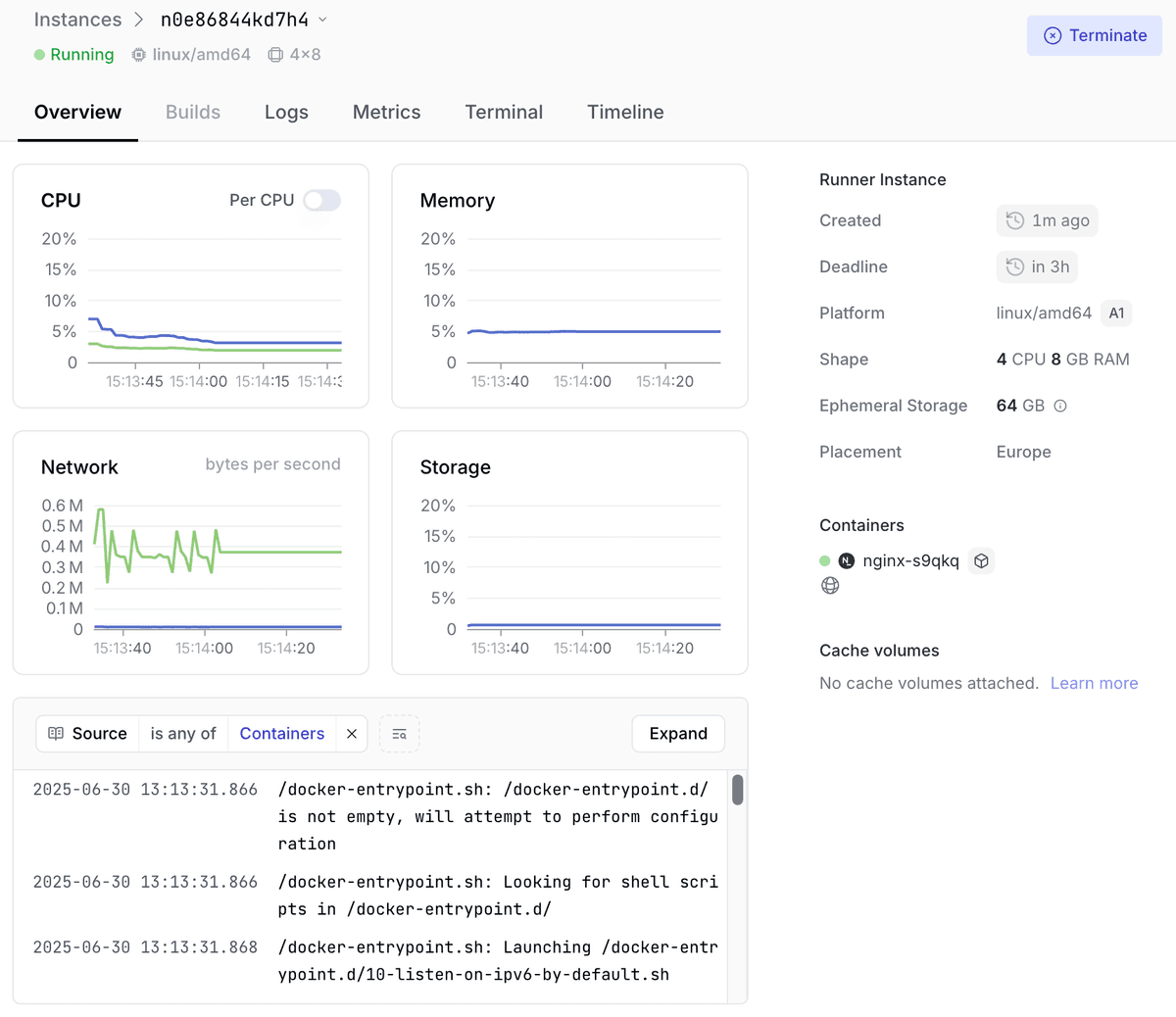
Monitoring and Debugging
By building on Namespace Compute, you directly benefit from its comprehensive observability features providing deep insights into preview environment performance and behavior.
- Real-time Logging Access centralized logs from all pods, from the CLI or the Dashboard.
- Performance Monitoring Track resource utilization and network performance.
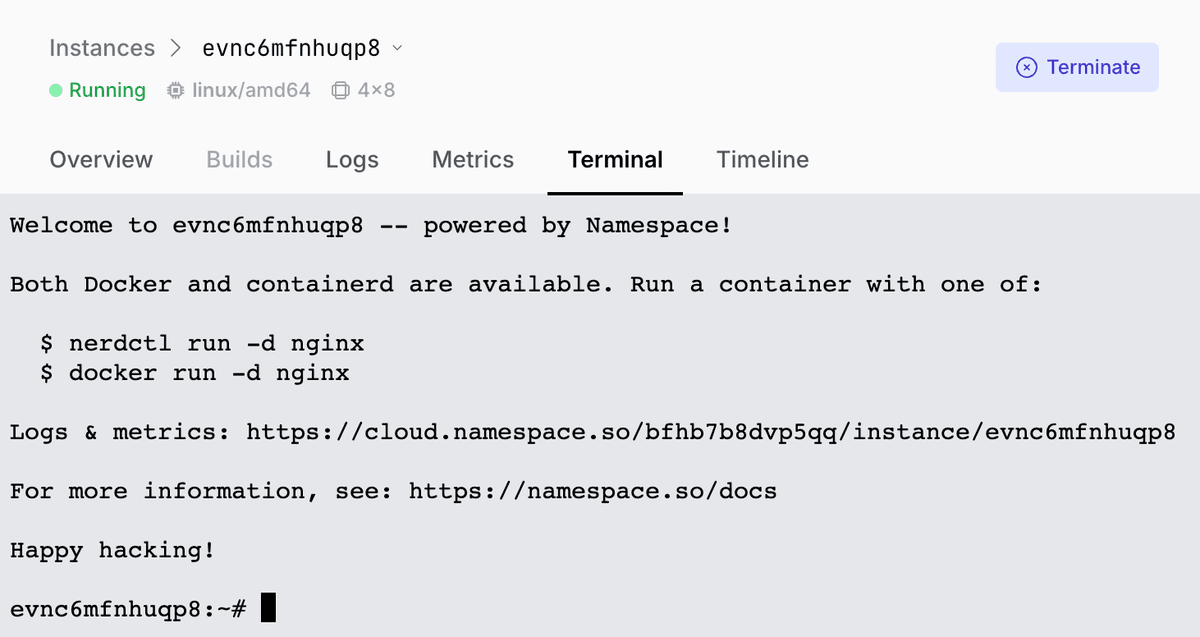
Namespace also grants root SSH access to each instance, allowing you to inspect the underlying infrastructure powering the preview.
Wildcard Ingresses
For complex applications requiring multiple endpoints or dynamic routing, Namespace supports wildcard ingress configurations. Wildcard ingresses excel in scenarios requiring microservice architectures with dynamic service discovery and when testing API gateways managing multiple backend services.
Enable wildcard support
Create an instance with wildcard ingress capability.
$nsc create --ingress wildcardThis outputs the ID of the created cluster, e.g.: 072higp5dg0bg
Start your application
Connect your local Docker to the remote preview environment.
$nsc docker attach-context --to 072higp5dg0bg --useUsing your existing tooling, you can now run your application in the preview.
$docker run --name nginx-foobar -p 80:80 -d nginxConfigure a wildcard ingress
$nsc expose container 072higp5dg0bg --wildcard --container nginx-foobar --container_port 80After creating a wildcard ingress, all subdomain traffic is routed to your specified service:
*.<instance-id>.<region>.namespaced.app